| Previous | Table of Contents | Next |
How A Firewall Restricts Access To Your Network
A firewall is an intermediary computer that stands between the Internet and your network. (See Figure 8.7.) A firewall basically performs the same tasks as the security guard at your office. The security guard will check your credentials at the door and then either let you in or refuse you access to the building. If your company allows visitors to enter the building, the guard may require visitors to sign a log book and show a proof of identity (like a drivers license) to verify that they are who they say they are. These two features—restricting access and logging access—are the fundamental functions that a firewall performs for your network.
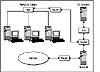
Figure 8.7 Using a firewall to protect your network.
A firewall restricts access to your network by using the information contained within a network packet. For Internet services that use the TCP/IP protocol, this information can be divided into five basic components, as summarized in Table 8.2. These basic components include the protocol, destination IP address, destination IP port, source IP address, and source IP port. As a comparison, consider the way you make a phone call. First, you pick up the telephone, then you dial a one (or perhaps you dial nine first to access an external line, if you call from work), the area code, and finally the seven-digit phone number. When the other party hears the phone ring, he or she picks up the phone and you begin your conversation. You might say something like, “Hello Valda, this is Art.” If you want the party (Valda) on the other end of the phone to call you back, you exchange phone numbers. When you have finished your conversation, you hang up the phone.
In this example, your area code could be considered as the source address, and you would be considered as the source port. The other party’s phone number would be the destination address, and he or she would be the destination port. The method you use to dial the number, initiate, then end the conversation, would be considered the protocol.
| Component | Description |
|---|---|
| Protocol | Transmission Control Protocol (TCP) or User Datagram Protocol (UDP). |
| Destination IP Address | Identifies the location of the computer receiving the data transmission. |
| Destination IP Port | Identifies the application on the computer that will receive the data transmission. |
| Source IP Address | Identifies the location of the computer initiating the data transmission. |
| Source IP Port | Identifies the application on the computer that initiates the data transmission. |
If your destination party’s phone company supports caller ID and your destination party has the appropriate hardware, then he or she can determine who is calling them before they pick up the phone. Some caller ID hardware devices can even record the number of the calling party (you) and the duration of the call. A firewall functions in a similar manner. By using the destination and source IP addresses and IP port information contained within a packet, the firewall can either accept or reject the packet. It can also accept or reject packets based on the protocol contained within the packet. The firewall can also log this activity, much as a caller ID hardware device does, to determine who is attempting to access the network.
Some firewalls go beyond the basic packet-filtering mechanism and utilize a network session as their key means to accept or reject network requests. A network session occurs at the user or application level rather than the IP transport level. Each network session will utilize a different IP port, so each session is guaranteed to have a unique identifier consisting of the five basic components previously described. Session-based firewalls offer increased security and more efficient client activity recording options. So, if you are looking at purchasing a firewall, check to see if it supports session-based security.
Many people consider a firewall as the only protection they need for their network. This is not true, however, because a firewall only filters information. If you close the filter completely, you are secure. But this also prevents you from utilizing any of the Internet resources. If you open the filter to provide access to the Internet, you are also creating a window of opportunity for someone to access your system. This follows the same analogy as the services provided by your security guard on the night shift. If he locks the building, he can prevent thefts from occurring. Of course, he also prevents any employees from entering the building and performing any work (such as cleaning the offices). By opening the doors of the building, the work can proceed. By making his rounds at night, he can help prevent thefts from occurring by his presence, but he cannot prevent all occurrences as he cannot be every place at once. All a security guard can do for you is lessen the chance of a theft occurring. All a firewall can do for you is lessen the risk associated with an Internet connection—it cannot entirely remove all risk.
| Previous | Table of Contents | Next |