| Previous | Table of Contents | Next |
Using A Proxy Server To Restrict Network Access
A proxy server is really another type of firewall. Rather than working at the packet level, a proxy server operates at the application level. This means, it also uses a network session as its primary means of denying access. But, a proxy server includes one additional feature not provided by session-based firewalls. It can mask the address and IP port of the source computer from the destination computer. This can prevent unauthorized access to your network while still providing access to external users. Let’s take a look at how proxy servers work in theory.
Assume for the moment that your network includes a server running the Internet Information Server on one computer and a proxy server, as shown in Figure 8.8. The IIS server and the proxy server are both connected to a router, which, in turn, is connected to the Internet. Your network clients’ only access to the Internet, however, is through the proxy server. So, all network traffic to or from these network clients and the Internet must go through the proxy server.
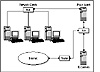
Figure 8.8 Using a proxy server to protect your network.
When you create your proxy server, you also assign an IP port address for the proxy server to monitor. You may assign one IP port address for all Internet services (such as WWW, FTP, Gopher, and so forth) or one port address for each Internet service. Your network clients will then connect to the port on your proxy server. The proxy server will determine the destination IP address and IP port the client wants to utilize. If the connection is not authorized, the connection will be terminated. If the connection is authorized, the proxy server will connect to the external source. As data is received from this external source, it is passed to the network client. Any requests from the network client will be passed to the external source, through the proxy server. In essence, the proxy server masquerades as the destination computer to the network client and as the network client to the destination computer.
In order for an external user to gain access to your internal network, the person would have to know the IP address of the client computer, the IP address of the proxy server, and the IP port the proxy server is monitoring. This person would also have to be on the allowed access list (usually based on the external clients IP address). If any of these items are unknown, the external user cannot connect to the client on the other side of the proxy server.
Using Multiple Network Protocols To Restrict Access
A less expensive and less secure method to limit potential access to your network is to use different network protocols on your internal network and your IIS server. You could use the IPX/SPX protocol on your internal network. You would then use both TCP/IP and IPX/SPX on your IIS server. (See Figure 8.9.) This way, your network clients would be isolated from external Internet users, but they would still be able to access the shared directories on the IIS server. In this fashion, you could provide a limited means of accessing data on an FTP site, for example.
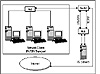
Figure 8.9 Using multiple protocols to protect your network.
The only drawback to this type of solution is that your network clients would not be able to access the Internet. However, there is a solution for multiple protocol-based networks. It is possible to use a gateway (another piece of hardware, or software, located between the network clients and the Internet connection) that would convert network requests from your clients using the IPX/SPX protocol to the corresponding TCP/IP protocol. This solution generally requires specially modified Internet utilities based on the IPX/SPX protocol rather than the standard Internet protocols.
Putting It All Together
Once you have determined the best network design, you actually have to build it. My personal preference and recommendation is to use a 10Base-T network with a star topology. If you can afford it, use fast Ethernet instead of 10Base-T. A star topology network performs well and requires little maintenance. Your choice of network protocols requires a bit more thought. I recommend you use NetBEUI for any network with less than 50 clients. From 50 through 100 clients, I suggest you use IPX/SPX. For anything more than 100 clients, I suggest you use TCP/IP. In some cases, however, you may need to use multiple protocols. You may even need to use multiple network adapters if you use your server to segment your network rather than use dedicated routers. Should this be the case, there are a few additional tips and tricks you can implement to improve your network performance.
| Previous | Table of Contents | Next |