| Previous | Table of Contents | Next |
Auditing The Registry
Should you encounter problems with registry keys, values, or data entries suddenly disappearing or changing, you may want to audit the registry to determine who may be changing the keys. You can also audit the registry to find out who may be trying to circumvent your security. This might occur, for example, when a user connects to your registry remotely and looks around for any unencrypted user accounts and passwords, such as when you use the AutoAdminLogon option as specified later in this chapter in the section titled “Useful Registry Keys.” To view the auditing information, use the Event Viewer, and look in the Security Log.
To audit a registry key, follow the steps presented here.
- 1. Select the registry key to audit, and choose Audit from the Security menu.
- 2. The Registry Key Auditing dialog box, shown in Figure 13.8, should appear.
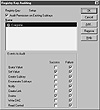
Figure 13.8 Auditing a registry key.- 3. Check the Audit Permission On Existing Subkeys to cascade your auditing requirements to all child keys, if desired.
- 4. Click the Add button to display the Add Users And Groups dialog box to specify the users or groups that you will audit when the user or group accesses the specified key(s). I normally specify the Everyone group, but in a large organization, this could generate a lot of auditing messages.
- 5. Once you have completed adding users or groups, click OK to close the Add Users And Groups dialog box and return to the Registry Key Auditing dialog box.
- 6. Next, select the events to audit in the Events To Audit group. You can choose to audit successful accesses or just failures to the specified key(s). The items you can audit include:
- • Query Value—Specifies to create an audit message when the selected user or group attempts to read the selected value entry.
- • Set Value—Specifies to create an audit message when the selected user or group attempts to write to the selected value entry.
- • Create Subkey—Specifies to create an audit message when the selected user or group attempts to create a new subkey.
- • Enumerate Subkey—Specifies to create an audit message when the selected user or group attempts to identify all subkeys and value entries of the selected key entry.
- • Notify—Specifies to create an audit message when the selected user or group attempts to receive notification events.
- • Create Link—Specifies to create an audit message when the selected user or group attempts to create a symbolic link to the selected key or value entry.
- • Delete—Specifies to create an audit message when the selected user or group attempts to delete the selected registry key or value entry.
- • Write DAC—Specifies to create an audit message when the selected user or group attempts to set a discretionary access control (DAC) list on the selected key or value entry.
- • Read Control—Specifies to create an audit message when the selected user or group attempts to read the permissions already set to the selected key or value entry.
- • Set Value—Specifies to create an audit message when the selected user or group attempts to write to the selected value entry.
- 7. Once you have specified your auditing requirements, click OK to return to the Registry Editor.
- 8. Repeat Steps 1 through 7 for each key to audit.
- 2. The Registry Key Auditing dialog box, shown in Figure 13.8, should appear.
Miscellaneous Registry Editor Commands
A couple of other Registry Editor menu options that can come in handy from time to time include the following:
- • Registry|Select Computer—Allows you to open a remote computer’s registry for you to manipulate, just as you would your own local registry.
- • Registry|Close—Closes a remote or local registry.
- • Registry|Open Local—Opens a local copy of your registry.
- • Registry|Print Subtree—Prints a copy of the selected registry key.
- • Registry|Save Subtree As—Saves a copy of the selected subtree in text format.
- • Security|Owner—Enables you to take ownership of a registry key.
- • View|Display Binary Data—Enables you to view selected binary data in a split hex dump format rather than the raw format.
- • Registry|Close—Closes a remote or local registry.
Repairing A Damaged Registry
Windows NT Server stores all configuration information in the registry, so if you damage the registry, you can be in serious trouble. If the registry is damaged too much, you may find that Windows NT Server may be unable to boot at all. This is really serious because it means that your entire network may be unusable. So, what can you do about this possible problem?
First, you can make regular system backups on tape and back up the registry at the same time. This is your first line of defense, and it should not be taken lightly. Any time you back up the system partition, back up the system registry, as well.
Secondly, you can use the Repair Disk Utility, shown in Figure 13.9, to back up the registry to a floppy or to the hidden directory SystemRoot\Repair. The Repair Disk Utility is called RDISK.EXE and is located in the SystemRoot\System32 directory. As long as your entire registry will fit onto a single floppy disk, you can restore your entire registry using the three boot disks that come with Windows NT Server using the Repair option of the setup program. Unfortunately, as your system grows in scope, you will find that your registry will no longer fit onto a single floppy. But if you update the repair information using the Update Repair Info button, you can often use this compressed registry information to restore your registry.
Figure 13.9 Updating your registry information.
| Previous | Table of Contents | Next |